XSS bugs on DMARC checking sites
We discovered several Cross Site Scripting (XSS) bugs on many sites including Agari.com, Mimecast.com, Dmarcly.com, and others that have online tools which help website owners validate DNS records of domain names.
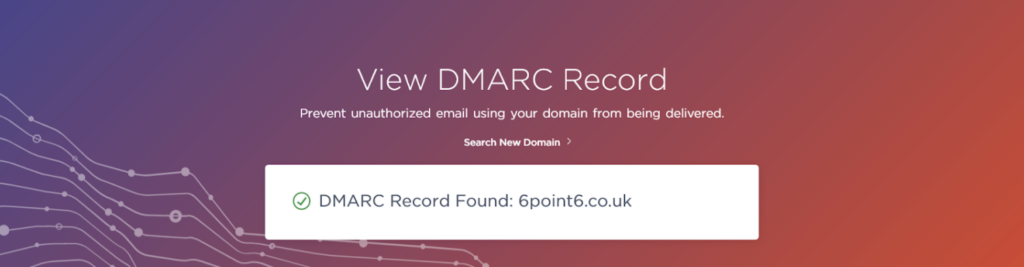
Our Cyber Lab team recently worked on a Domain-based Message Authentication, Reporting, and Conformance (DMARC) project, which reviewed email providers to see how they handled spoofed messages. We used our own test domain name so we could easily configure our own DMARC settings.
Using a standard DNS querying tool like ‘dig’ to verify records was enough but we also wanted to see if these “Online DMARC Checkers” were actually any good at identifying issues. The official DMARC website has a page for deploying and creating DMARC records and it also includes third party sites.
We decided to investigate whether these DMARC checkers would pick up domain names that contained malicious Javascript data within DNS records.
Agari
Agari provides email security services to enterprises helping them deal with phishing and spoofing attacks. It is also one of the co-founders of DMARC standard. During our banking investigation with Which?, we identified that Agari was used by many UK banks for DMARC reporting services.
A report is sent to the company’s email address (e.g. [email protected] or [email protected]) whenever an email fails authentication checks. The report contains information which is helpful for security analysts to detect phishing emails or other issues.
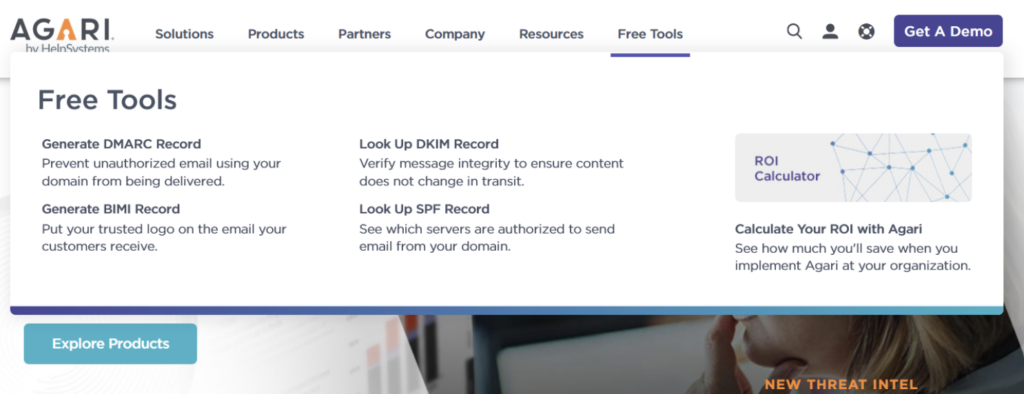
There are four online tools for checking domain records; DMARC, DKIM, BIMI and SPF records. Each tool has a web form where users can submit a domain name and click a button to process it.
On 29th March 2021, using our test domain name, we discovered that all tools except SPF were vulnerable to XSS. We were able to verify this by loading our Javascript code onto the page which simply showed a message box when we supplied our domain. Since this was on the root domain, it could’ve been abused to steal customers’ cookies and hijack accounts.
Below is a screenshot of Agari’s website showing our payload loaded onto the page:
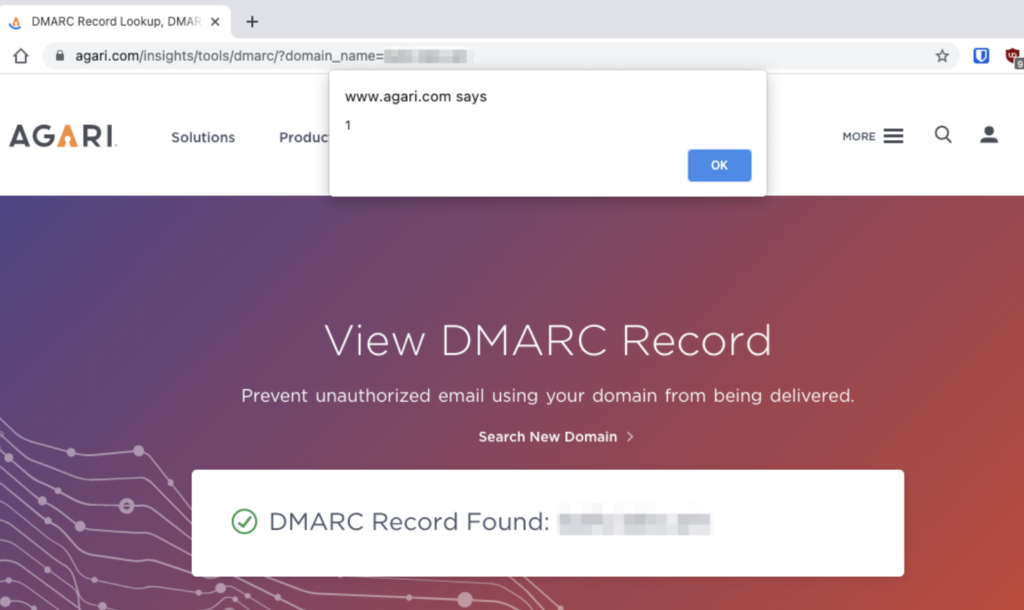
A security disclosure report was sent to their security team and within a few days they were able to fix the issues.
Mimecast
Mimecast is a well-known UK based company that provides email and web security services to a wide range of businesses and public organisations. Similar to Agari, Mimecast’s website contains a product called ‘DMARC Analyzer’.

On 29th March 2021, we discovered their DKIM checker tool was also vulnerable to XSS. Again, we were able to verify the issue by submitting the test domain name and getting the page to load our payload containing Javascript.
Below is a screenshot of Mimecast’s website showing our payload loaded onto the page:
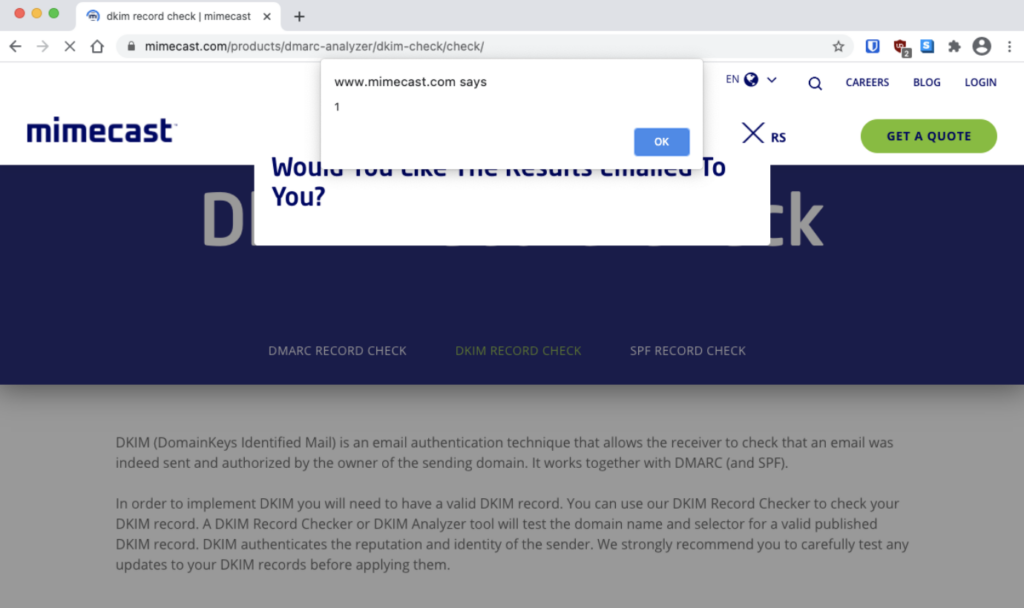
The issue we discovered revealed that the domain name could have been used to steal customers’ cookies and log-in sessions, attackers would also be able to bypass email filters for phishing emails containing links that whitelist the mimecast.com domain name. The payload would have redirected the victim to the intended destination URL.
A security disclosure report was written up, sent to their security team and the issue was fixed a few days later.
Dmarcly
We found another company that provides DMARC reporting services called Dmarcly.com.
On 29th March 2021, we discovered that the Brand Indicator Message Identification (BIMI) checker was vulnerable to XSS. BIMI is made so that a company’s familiar logo or brand is included within the email address avatar. This is not widely supported by email providers.
Below is a screenshot of Dmarcly’s website showing our payload loaded onto the page:
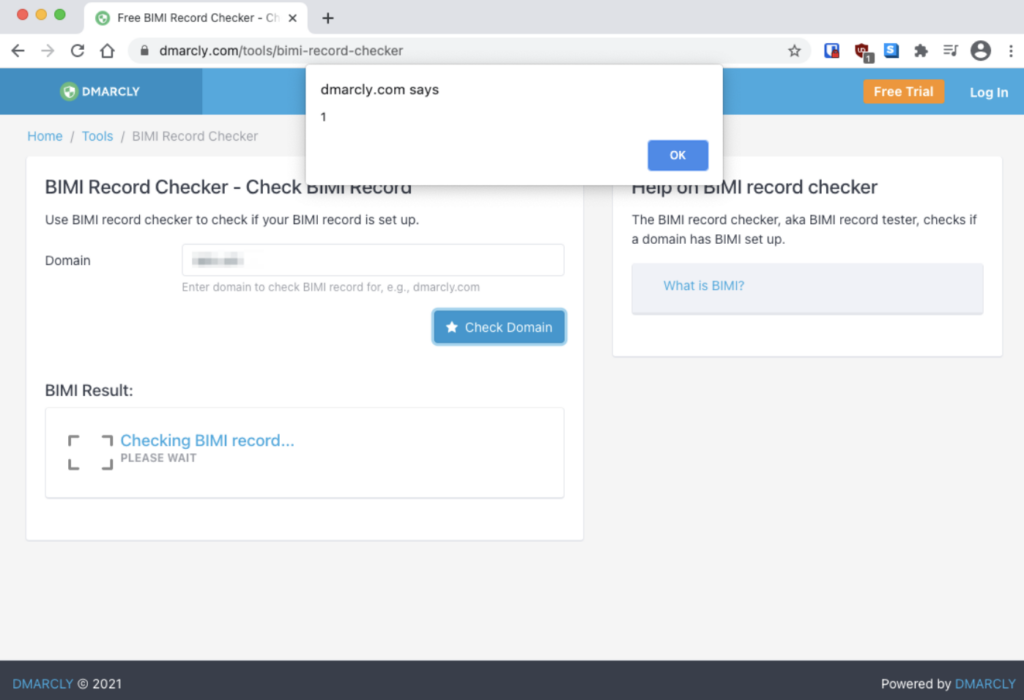
A security disclosure report was written up and sent to their security team. The issue has now been resolved.
What DNS TXT records did you use to test XSS?
For the testing domain we used three types of DNS TXT records. A DMARC record, a DKIM record and a BIMI record. All the provided examples contain a simple HTML code which opens a dialog with the number ‘1’, as soon as the page is loaded.
These examples should work on most web browsers. We also kept some valid data before the actual payload. Some checkers said our domain had valid DMARC records, even though it contained Javascript.
DMARC
A malicious TXT record (_dmarc.example.com) would look like this:
| v=DMARC1; p=reject; sp=reject; fo=1; rua=mailto:[email protected]; ruf=mailto:“</td><body onload=alert(1)>; |
DKIM
A malicious TXT record (default._domainkey.example.com) would look like this:
| v=DKIM1; h=sha256; k=rsa; p=MIIBIjANB…wIDAQAB;
n=“><body onload=alert(1)> |
BIMI
A malicious TXT record (default._bimi.example.com) would look like this:
| v=BIMI1; l=https://example.com.svg“><script>alert`1`</script> |
What DNS provider did we use?
We used Cloudflare for all of our testing.
Summary
This isn’t anything new. There have been many articles about researchers using malicious DNS records that exploit improper input validation on websites. Web developers sometimes forget to always treat user supplied input as hostile, including DNS records. All the vendors were notified about the issues. And after the 90 day period we have published this blog post. We would like to recognise Mimecast for quickly fixing the issue once they were notified.