Bottom of the telecoms stack: SIM cards
This blog is the first part in a series of mobile telecommunication topics. In it we cover what SIM cards are, how they keep user data secure, and what data they contain themselves. We will also be going through how SIM cards communicate with devices.
What are SIM cards?
Subscriber Identity Modules or SIM cards are smart cards that store cryptographic identifiable information of subscribers (the user). This provides a way for mobile network operators such as Vodafone and EE to identify and authenticate users before allowing access to the network.
The hardware component of a modern-day mobile smart card is called Universal Integrated Circuit Card (UICC), whereas the applications that run on it are called the SIM and USIM (Universal Subscriber Identity Module). Prior to the year 2000 both these components were referred to as a SIM. However, this change was necessary because it now included security improvements and longer encryption keys.
All UK mobile networks use UICC cards that have both applications, which gives backward compatibility in case there is service outage, or your mobile device doesn’t support the newer version.
Specifications
A SIM card includes the following:
- Microprocessor
- ROM – Read-only Memory (stores the code run on the microprocessor, and secret values)
- RAM – Random Access Memory
- EEPROM – Electrically Erasable Programmable Read-only Memory (stores the file-system)
- Operating System (Java Environment)
There are many different form factors of smart cards: mini (2FF), micro (3FF), nano (4FF) and MFF2 (eSIM). The nano is by far the most popular form factor in current handheld mobiles.
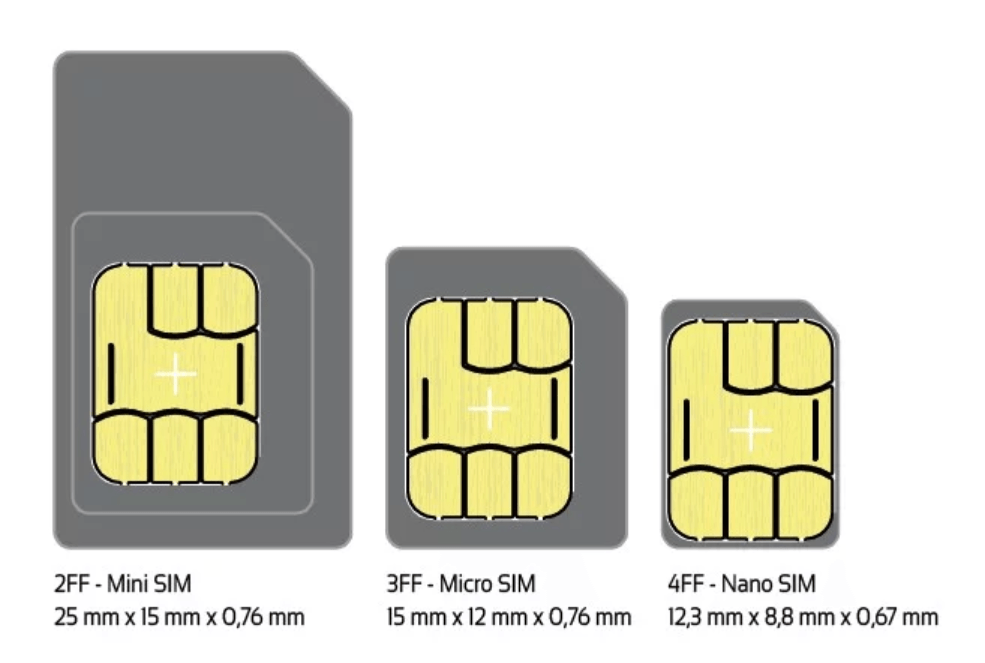
Figure 1: Physical SIM cards in three common sizes (from here).
SIMs have the ability to run applications called Applets, commonly installed by a network operator. This is achieved through the SIM Application Toolkit (SAT) interface. The SAT interface usually runs in the background and can detect changes such as whenever the SIM card has been inserted into a new device. Among other tasks, the SAT plays an important role in receiving ‘silent’ SMS messages, which do not notify the user like with traditional SMS messages. Network operators can use these messages to, for example, update roaming settings or install new applications.
File system and data
The SIM card’s file system resides on the EEPROM or flash memory and stores data in a hierarchical tree structure.
Data such as phone number, address books, text messages, and network operator settings can all found on the EEPROM. This area and other features can be protected by using an authentication PIN (Personal Identified Number).
We are still limited by what we can read off the SIM card. A study conducted in 2016 tested various forensics tools at how effective they were at retrieving SIM card information. Over 40 different kinds of information were examined (example in Table 1 below). These could be extracted, even after the SIM had been removed from a mobile device (Nada Ibrahim, 2016. Forensic Investigation of SIM Card).
| Description | Value | ||
|
ICCID |
Integrated Circuit Card Identifier is a unique value associated to the physical UICC card and not the subscriber. |
89441000000000000018 |
|
|
IMSI |
International Mobile Identity is a unique value associated to the subscriber on the network.
|
234150000000649 |
|
|
IMEI |
International Mobile Equipment Identifier is a unique code associated to the modem or handheld device.
|
356500009800778 |
|
|
MSISDN |
Mobile Station International Subscriber Directory Number is a mobile phone number used in making and receiving calls.
|
07000007068 |
|
|
TAC |
Tracking Area Code is a unique code for network operators assign to associated tracking area location. |
1588 |
|
Table 1: Examples of different data along with their description stored on a SIM card
There are three types of files: Master File (MF) – the root of the file system directory, Dedicated Files (DF) – sub-directories of the master file directory, and Elementary Files (EF) – containing the actual data in various sizes and types. An example of a SIM card file system hierarchy is shown in Figure 2 below.
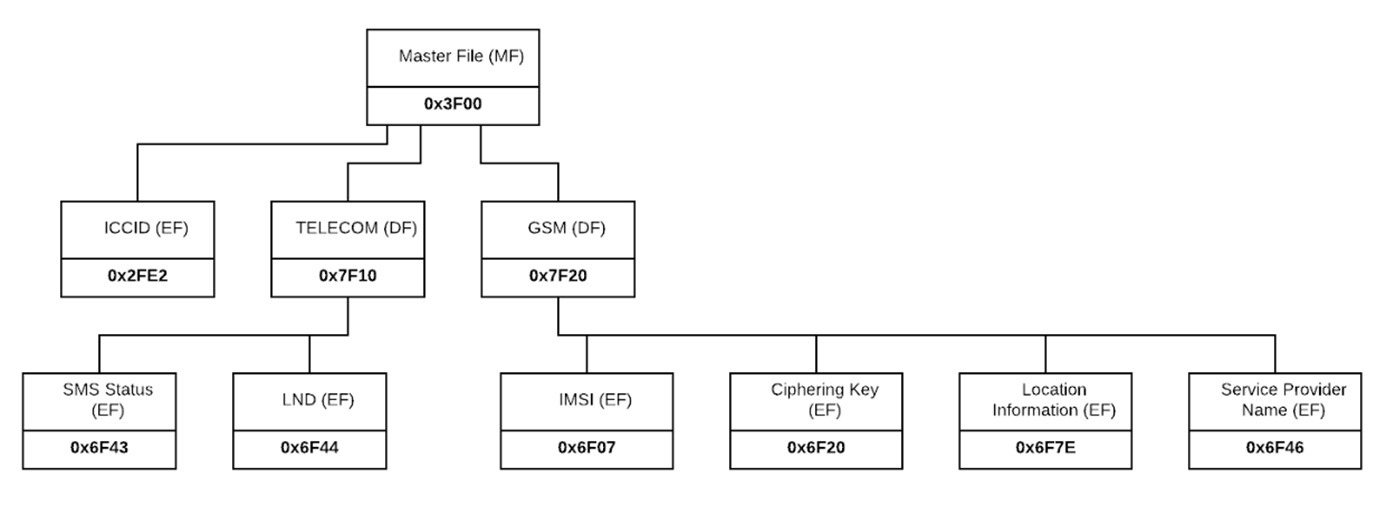
Figure 2: An example of GSM SIM card tree hierarchy with file headers
Usage in 2G, 3G, 4G and 5G
All SIM cards contain cryptographic keys. The secret authentication key called Ki (pronounced K-I) is unique and is stored on the ROM, a protected area of the SIM. The Ki is never exchanged between the mobile device and the network. Its purpose is to derive sub-keys that perform the necessary authentication procedures when a mobile device tries to join a carrier’s network. The Ki is also stored on the carrier’s network within a component called the Authentication Centre, or a Home Subscriber Server, depending on the technology used.
Security comparison
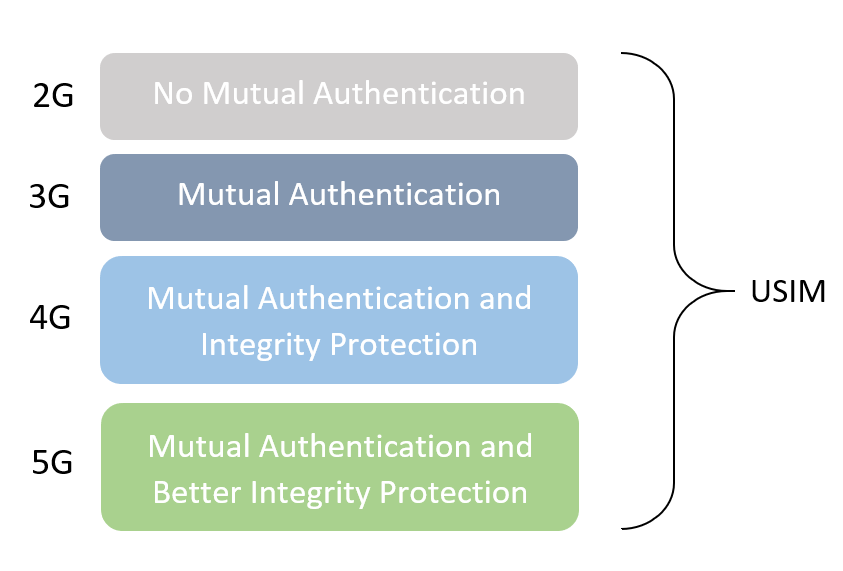
Key points:
- 2G GPRS – 64-bit key length, weak A5/1 stream cipher, no mutual authentication (i.e. the SIM is authenticated by the base station).
- 3G UMTS – 128-bit key length, improved authentication algorithm (A5/3), and mutual authentication (both the mobile device and network authenticate each other).
- 4G LTE – 128-bit key length, increased number of cryptographic keys and new security algorithms, full TCP/IP back-end increasing bandwidth.
- 5G NR – supports three different authentication methods, uses public key encryption and additional keys.
SIM swapping
Very much a current security issue, SIM Swapping is a form of social engineering. An attacker tries to convince a mobile carrier to change a phone number to another. This has been seen many times.
For example, in 2019 a Twitter user with over 4.2 million followers had his account compromised when attackers were able to assign his phone number to themselves. A few mobile carriers can add an extra layer of protection such as a unique code that would be required when a subscriber decides to change network or their number.
Weaknesses of mobile handsets
When handsets roam into an area not covered by 5G or 4G, or if the service is significantly degraded, mobile devices will attempt to establish a connection with an older technology (LTE > UMTS > GSM). This creates an opportunity for attackers to manufacture a fake base station that mimics a real cell tower and compromise the integrity and security of the connection. In a future post, we’ll show how it’s possible for attackers to spoof emergency alert messages on mobile devices by creating a fake LTE base station.
You can disable support for 2G on your phone settings to only allow 4G and 3G, which is significantly more secure. However, if you’re in a location that only supports 2G you’ll have no service.
Reading and writing to SIM Cards
When a mobile device communicates with the SIM card, it uses Application Protocol Data Units (APDUs) which have six key parameter fields. Without getting into too much detail, these are: Class, Instruction, Parameter1, Parameter2, Length, Data and another Length field. APDU commands must consist of at least 4 bytes.
| Instruct | Param 1 | Param 2 | Length* | Data* | |
| SELECT | A4 | 00 | 00 | 02 | – |
| Read Binary | B0 | Offset high | Offset low | Length | – |
| Update Binary | D6 | Offset high | Offset low | Length | – |
| Verify PIN | 20 | 00 | ID | 08 | – |
| Run GSM Function | 88 | 00 | 00 | 10 | – |
Table 2: APDU commands for communicating with SIM cards, last two fields with (*) are optional.
When a mobile device sends an ADPU command, the SIM card processes the request and sends a response back to the mobile device. The APDU response has two fields, a body field which contains the actual data, and two status codes (SW1 and SW2) which tell us if a command was successful. In example, the table below shows a successful response.
| Body | SW1 | SW2 |
| Response data | 90 | 00 |
A complete list of all APDU responses can be found here.
Here is an example of retrieving an IMSI value from a SIM card using raw APDU commands. The ‘>’ signifies requests are being sent to the SIM card and ‘<’ signifies the response from the SIM card.
Note: for each command line the first byte is always A0 which is the Class, as were communicating with a SIM application. On an USIM application this would be 00 instead.
[1]
> A0 A4 00 00 02 3F 00
< 9F 16
[2]
> A0 A4 00 00 02 7F 20
< 9F 16
[3]
> A0 A4 00 00 02 6F 07
> 9F 0F
[4]
> A0 B0 00 00 09
< 08 29 43 62 02 21 28 62 02 90 00
Each line is described below:
- Select the Master File at the offset 3F 00. The response received (command successfully executed) with 16 bytes of data.
- Select the Dedicated File ‘GSM’ at the offset 7F 20. The response received (command successfully executed) with 16 bytes of data.
- Select the Elementary File ‘IMSI’ at the offset 6F 07. The response received (command successfully executed) with 9 bytes of data.
- Read binary file of 9 bytes. The response received is raw APDU IMSI which is encoded in TLV (Tag Length Value) and the last two bytes confirming the command was successful.
Writing to commercial SIM cards like Vodafone or O2 would not be possible, because restrictions are put into place stopping users from modifying data. However, it is still possible to unlock write features by supplying an administrative code that only the network operator should know.
Using a mobile phone to Examine SIMs
The advantage of using a mobile device to examine SIM data is that we are able to analyse in real time. This data includes temporary values, signal strength, base station identity and other values. If the mobile device was turned off or not connected to a network, this information would be unavailable, although the SIM still retains records of the last used base station along with other data (i.e. the 40 bits of information discussed above).
AT Commands
AT is an abbreviation of ATtention. Attention commands are used to send instructions to the modem. Commands always start with the two letters ‘AT’, a string of additional parameters, and the response presented to the user.
Many older generation mobile devices have supported this feature since GSM, but newer devices have this feature disabled. In the example below we used a Nokia TA-1034 and a tool called ‘NokiaTool’ which is available here This enabled us to control the device over an undocumented serial connection through USB.

Figure 3: A Nokia TA-1034 connected to a USB port
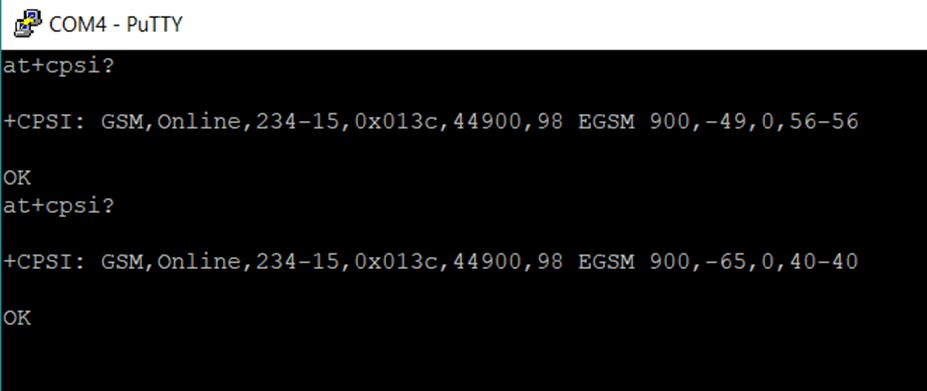
Figure 4: Running a ‘AT+CPSI?’ to print network service information of a Nokia device
The information received from the modem above includes – status, network code, base station identity, radio frequency, and signal strength. It may be possible to communicate with the device’s modem to send AT commands while in recovery mode i.e. Android devices.
This is an example of retrieving the TMSI (Temporary Mobile Subscriber Identifier) and Location values (0x6F7E) using raw ADPU commands on the Nokia phone:
| AT+CRSM=176,28542,0,0,11
+CRSM: 144,0,”2A654DB932F451008B0000″
TMSI LOC A6 54 DB 93 2F 45 10 08 B0 000 |
On the first line the value 176 is equal to B0 in hexadecimal which is the command to read binary.
Using a smart card reader
A smart card reader is a hardware module that interacts with smart cards (SIM cards). The smart card reader used in our example is called the Trust Token (Identiv uTrust 3512) reader. It supports all major ISO/IEC 7816 compliant standards and is compatible with Linux, Unix, and Windows operating systems. The device uses a standard USB 2.0 interface for communication which also require drivers to be installed on Windows computers to function properly.
Below is a list of applications that were tested which supported our reader device.
SIM Personalize Tool – a SIM and USIM programming tool available on Windows being used to write to the SIM and update KI secret key, IMSI and OPC values.
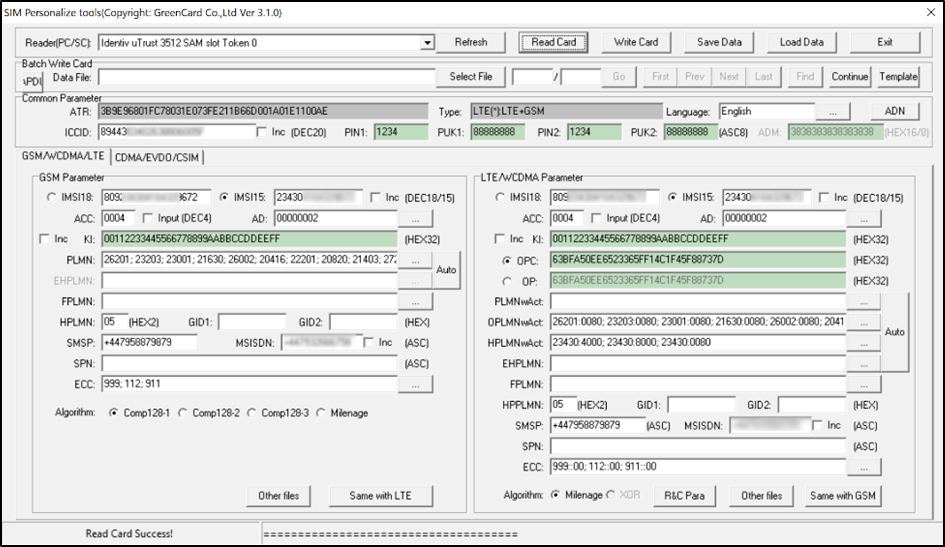
Figure 6: Reading a USIM using SIM Personalize Tool
Dekart SIM Manager – a SIM card viewer (limited visibility) available on Windows can be used to navigate to folders containing contacts, SMS messages, and other information.
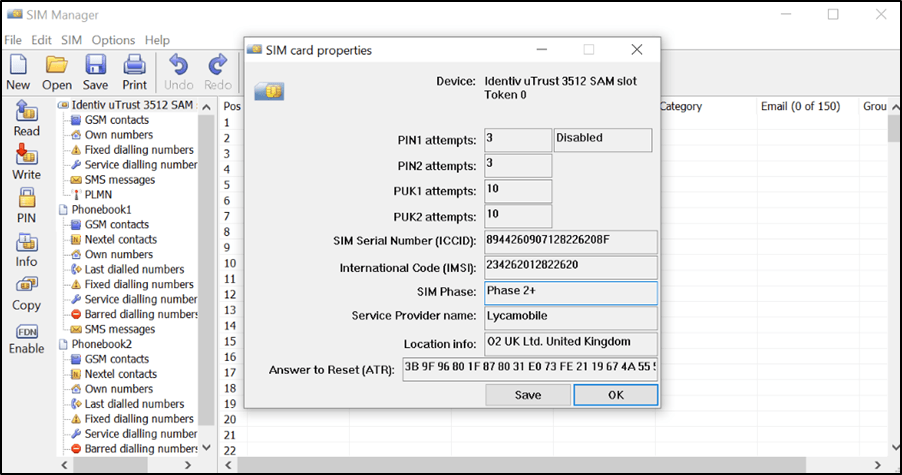
Figure 7: Reading a GSM SIM card using SIM Manager
pySIM – Python tool that can read and write to SIM and USIM smart cards. Available on Github.
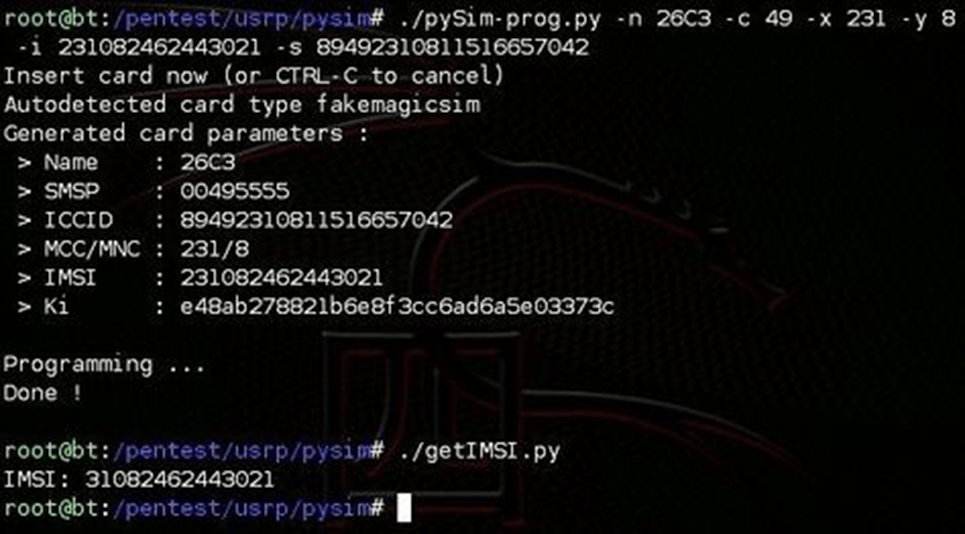
Figure 8: PySIM writing to a SIM card on a Linux system
For our latest research, and for links and comments on other research, follow our Lab on Twitter.
Alternatively, get in touch if you’d like to chat to us.