How can purple teaming prepare your organisation for ransomware attacks?
If a ransomware attack gets to the point where you’re debating whether to pay the attackers, it’s gone too far. Organisations can be better prepared to detect ransomware attacks before systems are encrypted.
Where are we with ransomware?
Ransomware operators and developers are continuously evolving. From their opportunistic roots to the now common Ransomware as a service (RaaS), the effectiveness of ransomware operations has improved drastically.
Early attacks like notPetya and WannaCry were self-propagating and operators had no control over the extent of the compromise. This caused huge disruption to organisations and a lack of targeting within the attacks resulted in no real promise of a payout for the attackers.
More recently we’re seeing highly effective, targeted deployments, with attack groups conducting operations more like nation state attackers. These attacks span the full attack life cycle including double extortion, meaning that alongside the traditional attack motive of encrypting your organisation’s systems, there’s the additional motive of stealing your data as well as.
We’ve also seen a rise in partnership models, such as REvil. This is where criminal groups provide a RaaS platform so that other bad actors can carry out attacks. Historically, the time from initial compromise to encryption was months, but we’re now seeing this reduced to weeks and even days.
Detecting attacks early
The view that attackers only need to succeed once but defenders need to succeed every time is outdated. It implies that getting into an environment is the end goal of an attacker which is not the case. The goal is to cause maximum disruption, and more recently with double extortion, there’s the added aim of disclosing sensitive data to force organisations to pay the attackers substantial sums of money.
Ransom attacks aren’t going away, but if your organisation can detect them early and prevent the attackers from successfully completing their mission, you can reduce how likely it is for your organisation to appear on ransom demand sites.
It’s not all about the encryption
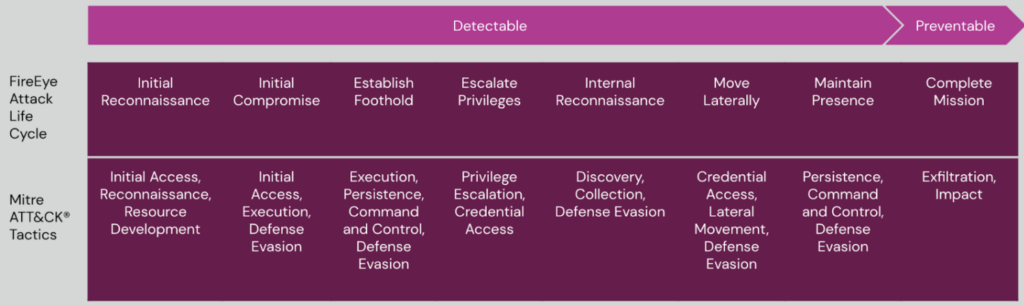
For ransomware operators to get to the point of stealing data or encrypting systems, there are several steps they must complete. These steps are well described in both the FireEye Attack Life Cycle, and in Mitre ATT&CK® Tactics.
Across the lifecycle of a breach, there are many stages which are detectable. Identifying this activity and stopping an attack mid-flight can prevent or disrupt its final stages.
By using purple teaming, organisations can identify where they are stronger or weaker at detecting common attack techniques and build a roadmap to effectively detect activity in this lifecycle.
What is purple teaming?
Purple teaming combines technical expertise to ensure a valued outcome for your organisation. It uses elements of red teaming, by assessing your incident response capabilities though simulating real world threat actors and scenarios. But this is done in combination with a blue team, assisted by our experts, to build and develop the capabilities you need to defend against future attacks.
Purple teaming simulates a broad range of threat actor capabilities to determine how effective your detection is. And it includes gap analysis so your organisation can uplift its capabilities going forward.
Are you ready for purple teaming?
Whether you’re ready for purple teaming depends on your organisation’s maturity. For example, running a purple team exercise if your organisation doesn’t have the basics in place offers little benefit as you first need to have the processes and technologies needed for detection and prevention capabilities in place.
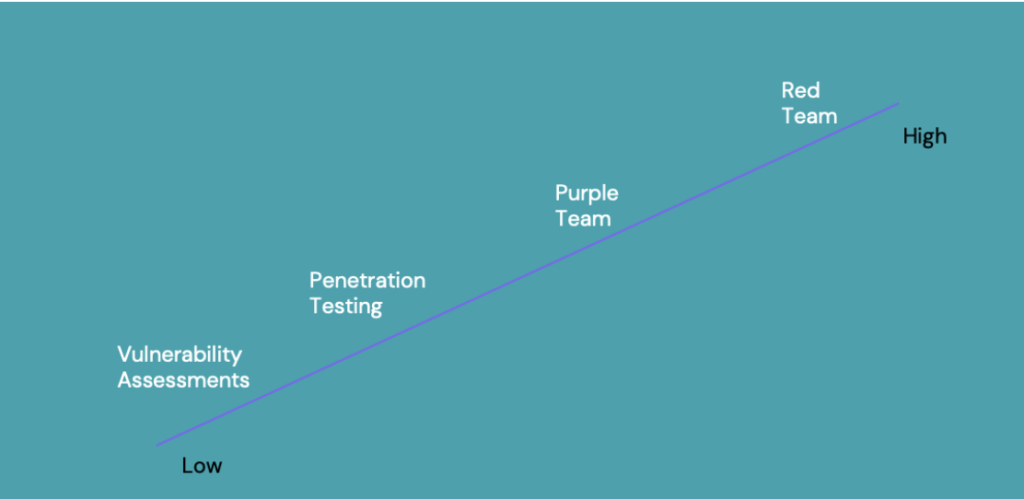
Purple teaming sits between penetration testing and red teaming for effectiveness in organisations. It bridges the gap between them and helps organisations who are in the lower half and middle of the scale. These types of organisations are also, ultimately, the usual victims of ransomware breaches.
Preventing disruption is key
Using purple team testing to understand the gaps in your detection and response capabilities, and then uplifting them where possible, means you’ll be better equipped to face attacks in the future.
No organisation can stop attacks from happening, but you may be able to deter attackers by making their job much harder. The less they’re able to effectively move around your organisation, the less likely they will be successful.
You’ll also be laying the foundations for red teaming as your organisation matures so that as the risks grow, so do your defence capabilities.
How we can help
When we provide purple teaming, some of our experts will join your blue team. We’ll guide you through all the stages of the purple team lifecycle and help you defend against a red team attack. We’ll also work with you through gap analysis to identify where you can upskill your team.
Get in touch if you’d like to chat to us.