Is the hotel industry getting left behind when it comes to cybersecurity?
Plenty has been written about the £99.2m fine issued to the Marriott group by the Information Commissioner’s Office (ICO) last year. As we all know by now, it was given to the hotel chain for its mishandling of a hack that led to the records of 383 million guests being compromised. It demonstrated with startling clarity the regulator’s extensive powers when resolving breaches of the General Data Protection Regulation (GDPR). It set a precedent that should provide the motivation for all organisations, across all sectors, to take cybersecurity seriously. It is also worth remembering that the fine, whilst unprecedented, was only half what it could have potentially been. The ICO has the power to fine an organisation up to 4% of its total annual worldwide turnover (in the preceding financial year), meaning this could have been even worse for Marriott.
The hotel industry is particularly vulnerable to cyberattacks because of the nature of its business operations. Hotel chains rely on complex IT systems that typically include partner and third party integration, but also need to make it easy for guests, any one of whom could be an attacker, to access their buildings and networks. This provides a large surface area for attack. Hackers have taken notice: they have developed a variety of techniques that are specifically designed to target the hotel industry, including:
- Phishing: This remains the most prevalent and effective means of cyberattack. The more sophisticated phishing campaigns are often augmented by inside knowledge on the target.
- Web applications: Web applications are a very easy target for hackers because they can be attacked remotely via the Internet. Hotel websites typically store lots of customer and payment data on their back-end systems.
- Denial of Service (DoS) attacks: Multiple hotels have reported availability issues with their room management and booking systems due to DoS attacks. In at least one case this forced the hotel to revert to paper-based systems.
- Point of Sales (PoS) devices: Hackers install malware on PoS devices that allows them to ‘skim’ customer payment information. This data can then be leveraged for financial gain.
- Wi-Fi: Without the appropriate design and configuration, Wi-Fi provides hackers with an entry point through which to mount attacks on other guests and any connected network or physical system.
- Ransomware: The primary purpose of a ransomware attack is to deny the target’s access to sensitive information in order to blackmail them for financial gain.
- Digital door locks: A vulnerability was found in one of the most widely used digital lock systems. The attack became so popular it was used in the TV show Mr Robot, while also appeared in numerous YouTube videos.
Statista’s research found that the food and hospitality industries, on average, spent significantly less on cybersecurity than the other eleven sectors surveyed. The graphic below demonstrates the startling disparity with other industries.
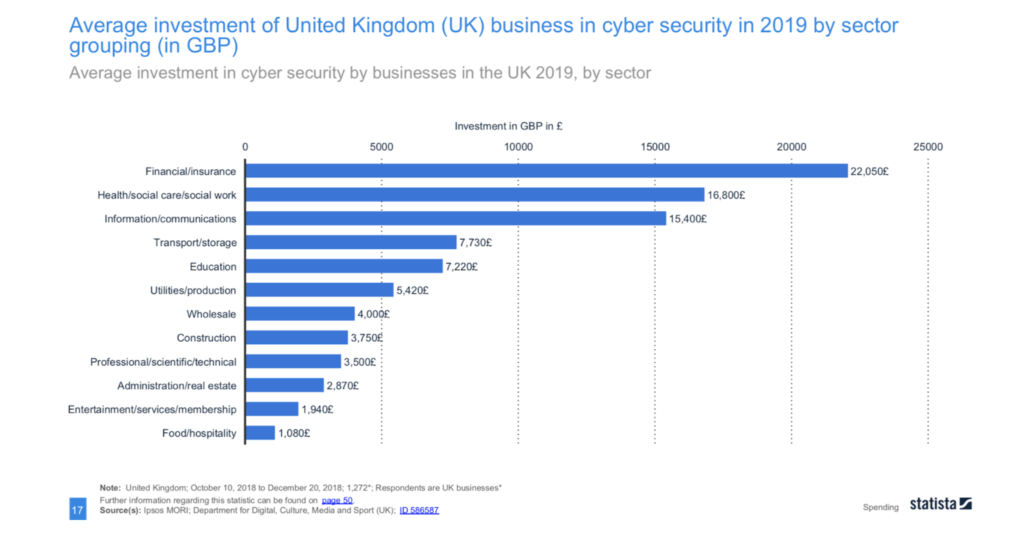
Trustwave’s 2018 Global Security Report identified hospitality as one of three industries particularly vulnerable to payment card breaches, while the 2019 version found that it had the third largest share of incidents across all sectors. The hotel industry has been slow to invest in IT security due to two popular myths:
Good security practices cannot be implemented without sacrificing good service. Increased cyber awareness means that guests value and actively look for signs that their data and devices are being well protected. This enhanced feeling of safety now adds to the guest experience. Good, demonstrable security measures and policies are now a fundamental component of a good service. This is especially true of high-value and high-threat individuals.
Greater profits can be made by saving on investment in cybersecurity. Perhaps once true, but this is no longer an excuse. New GDPR rules allow regulators to fine an organisation up to 4% of its annual revenue for poor cybersecurity practices, which is significant for any business. Loss of revenue through regulatory fines, legal action and reputational damage are all at stake.
What can be done?
There are endless IT security products and services on the market, and it can be a confusing landscape to navigate without the correct level of expertise and experience. The most important thing for an organisation is to ensure that there is someone responsible for cybersecurity inside the business, and that they are supported with the appropriate level of training and budget to perform the role. This may include utilising outside resources to fill gaps in skill, experience or capacity.
6point6’s recommendations
Maturity Assessment
Our recommendation at 6point6 is to perform a full review of your organisation’s current security state. Our methodology is tailored to the specific requirements and risk profile of companies operating in the hospitality and travel industries, including all of the following:
- New and existing web and mobile applications – for example, guest registration, loyalty programmes and booking systems
- New and existing infrastructure – for example, payment systems, WiFi, automated access control security systems
- Physical devices – for example, automated access control security systems, smart TV’s and entertainment systems, HVAC and lighting systems
- Supply chain: A businesses supply chain can become a target for attackers if they identify a weakness in third party applications or infrastructure that allows them to circumvent your security systems. Hotels are often required to share large volumes of data with their supply chain, meaning it is equally critical that third party systems are assessed and scrutinised to the same extent as your own organisation’s.
Penetration Testing
Penetration Testing is a popular and cost effective means of understanding how exposed your business is to a cyber attack. Our experts will identify security vulnerabilities across your business, and then exploit them in a controlled manner to demonstrate their potential impact on the business. By investigating your security vulnerabilities in a secure environment, you can begin to understand how to mitigate the risks these vulnerabilities pose. Penetration Testing allows your business to evaluate how exposed its assets are to hacking and the types of attack you’re likely to encounter.
For more tailored recommendations based on your specific business requirements, get in touch if you’d like to chat to us
Written by Misha Newman, Head of Red Team